AMSI Bypass alias AMSI Write Raid Vulnerability
- Ts3c
- AMSI , Red Teaming , Hacking
- June 2, 2024
tl;dr
Offsec published a couple of weeks ago their research of a technique to bypass AMSI without using the VirtualProtect API and without changing memory protection. Due to the researcher it should be possible to PowerShell 5.1 and PowerShell 7.4.
What is AMSI?
AMSI, or Anti-Malware Scan Interface, is a security technology introduced by Microsoft that allows applications and services to integrate with any antivirus software installed on a Windows system. AMSI provides a standardized interface for malware detection, offering applications the ability to call upon the installed antivirus engine to scan for and mitigate potential threats. This interface is particularly useful for detecting and preventing the execution of malicious scripts, such as those written in PowerShell, JavaScript, and other scripting languages commonly used in cyber attacks.
AMSI works by providing a set of APIs (Application Programming Interfaces) that applications can use to submit content for scanning. The antivirus engine can then analyze the content and return a verdict, which helps the application decide whether to proceed with the execution of the content or to block it if a threat is detected. This integration enhances the overall security posture of the system by enabling real-time scanning and threat mitigation.
VirtualProtect API and Memory Protection
The VirtualProtect API is a function provided by the Windows operating system that allows developers to dynamically change the access permissions of a region of memory. It is commonly used in software development to control how memory is accessed and manipulated by programs.
In the context of malware development, the VirtualProtect API can be exploited to manipulate memory protection settings for malicious purposes. Malware authors may use this API to alter the memory protection attributes of their code or data in order to evade detection, escalate privileges, or execute malicious actions without being detected by security software.
Memory protection in the context of malware development refers to the techniques used to prevent unauthorized access or modification of memory regions by malicious code. By leveraging the VirtualProtect API, malware developers can modify memory protection settings to make their code or data more difficult to detect and analyze by security tools.
Overall, the VirtualProtect API and memory protection play significant roles in the development and deployment of malware, allowing attackers to conceal their malicious activities and evade detection by security measures.
Make the bypass work
After reading this research by offsec I was hyped and immedtiatley want to try it on my own. I cloned the GitHub Repository and tried to execute the POC.ps1 out of the box.
Well that didn’t work.
Ok but why? Yes everything you will find on the internet is heavily flagged and will not work long enough.
So that means, that we need to make some changes in order to make this wonderful piece to work.
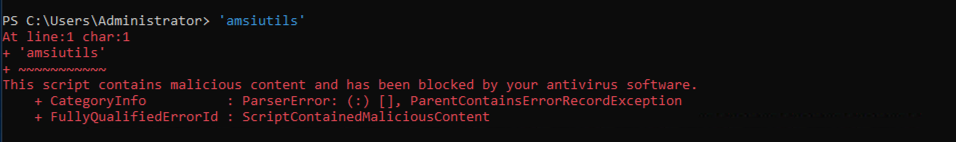
First let us verify if AMSI is activated on our target machine.
I am trying this bypass technique on an Windows Server 2022 Machine with the following specs:
As I said I tried the POC.ps1 out-of-the-box and it does not work. I checked the logs and saw that AMSI successfully found this Thread and stopped it from being executed.
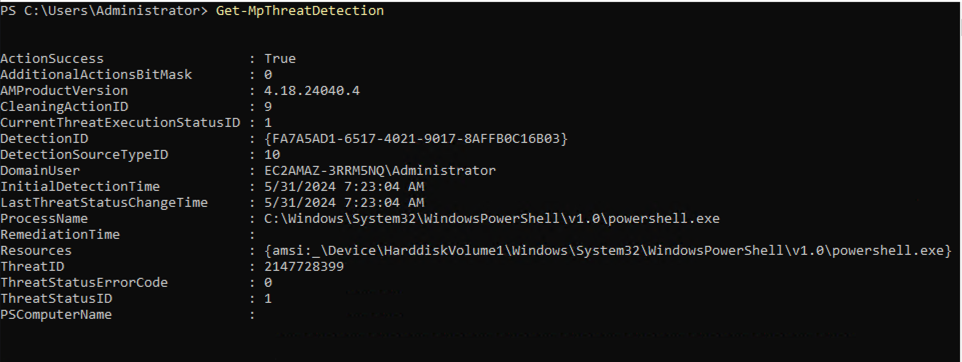
Now it is time to get our hands dirty.
To analyse if AMSI will get triggered while running some piece of spicy and delicious malware we can use ThreatCheck.exe to check this behaviour before using it in production. But keep in mind that is method as no 100% guarantee. There is still a chance that even if ThreatCheck does not find any Threat that AMSI in real life will.
Using ThreatCheck is really straight forward.
Run it on the POC.ps1 Code and you will receive the following output:
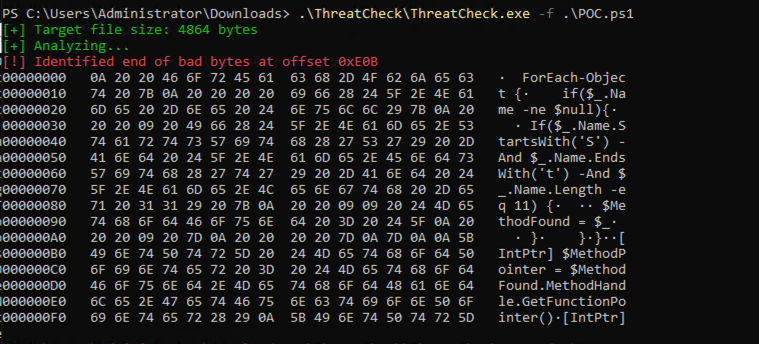
The interesting part is on the right hand side. This crap of output is the part AMSI get suspicious about. A ForEach-Object Loop some if conditions and I don’t know what.
Jumping into the Code and searching for this piece of code. After we found this part we need to change it in a way that will not get flagged by AMSI and the code needs to be working as intended.
This steps needs to be repeated a couple of times. Run ThreatCheck.exe, Search for the malicious part, change it but in a way that it still works as expected, run ThreatCheck.exe and repeat until you receive the output that no Threat was found.
Green is always a good sign.
Now we switch to our Victim Windows Machine and try our new modified AMSI Bypass.
Simply copy and paste the code into the Powershell Terminal and click Enter. After a couple of seconds nothing should happen. Nice. Lets run the following command and see if we get an output.
MagicBypass -InitialStart 0x50000
Now we can run the AMSI test string again and verify that we have successfully bypassed AMSI.
This could be behaviour can be tested with the simple string amsiutils. When AMSI would be still working than this command will get blocked from execution.

Video PoC
Final Thoughts
Great technique to bypass AMSI. More important to understand what you are really doing. Never just download a piece of code and execute it on your own production environment. It definetly will be malicous.
Thanks for reading!
Cheers and Happy Hacking!
Resources
https://learn.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal
https://learn.microsoft.com/en-us/windows/win32/api/memoryapi/nf-memoryapi-virtualprotect
https://www.offsec.com/offsec/amsi-write-raid-0day-vulnerability/

